Navigating Industry Challenges with Insights from OECM’s Supplier Partners
Introducing OECM’s Industry Spotlight

OECM’s quarterly Industry Spotlight news resource provides customers with access to various supply chain and industry-related insights and trends gathered and analyzed by our Supplier Relationship Management (SRM) team. This includes up-to-date information on the various challenges our supplier partners are navigating, post-pandemic, as well as environmental, social, and economic factors that are impacting our industries, and more.
In this second installment, we explore industry insights related to a timely and relevant topic that impacts OECM, its customers and its stakeholders – Cybersecurity.
Here, our team looks at rising cybersecurity concerns and threats, and dives deeper into why public sector organizations are more often the target of cyber criminals and identify OECM agreements available to help our customers across the broader public sector navigate these challenges.
Industry Insights: Cyberattacks and the Public Sector
Cyberattacks are more widespread and malevolent than ever before. With the recent wave of high-profile cyberattacks on major Ontario hospitals, school systems and government enterprises, it’s clear that in today’s unpredictable environment, public sector organizations are at particularly high risk. With more complex and volatile attacks, deep-seated cybercriminal networks, and advanced persistent threat (APT) groups that have greater access to technology which enables the development of malware, scripting and other tools used by potential hackers, the threat landscape is tougher than ever to navigate.
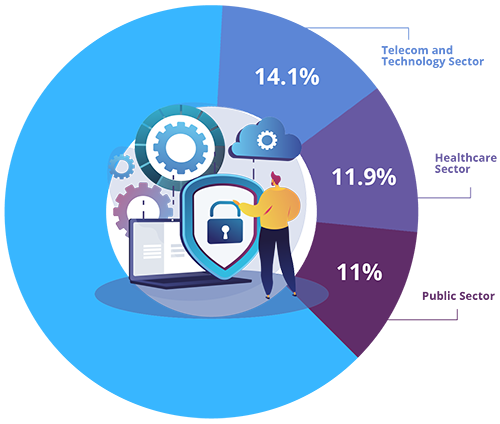
No organization is out of scope – cyber attacks affect not-for-profits, healthcare, and education, with government and public sector entities squarely in the crosshairs of cybercriminals. According to PwC Canada, only the telecom and technology sector experienced a larger proportion of attacks (14.1%) than the healthcare sector (11.9%) and public sector (11%) in Canada in the last year.
Furthermore, PwC Canada notes that government and public-sector entities are highly attractive targets of cyberattacks for the following reasons:
- They hold significant volumes of highly coveted data
- They are perceived to have virtually unlimited financial resources
- They have often underinvested in cybersecurity, and are struggling to modernize legacy systems as well as attract and retain talented cyber professionals to their organizations
This means that government and public-sector organizations are likely to continue to be among the top targets of cyber criminals seeking financial gain or competitive intelligence in the coming years.
OECM recently collaborated with five of our Information Technology (IT) supplier partners to delve deeper into the dangers of cyberattacks on public sector organizations. Our latest, Warning: You’ve been Infected! features industry-led insights that deconstruct the threat of cyberattacks to the public sector, while highlighting available prevention strategies, cyber resiliency programs and post-attack recovery action plans.
CYBER RESILIENCY: PLANNING AHEAD

While the cases of cyber threats and the landscape overall are expected to continue to grow exponentially due to increased hybrid cloud adoption and remote/work-from-home models, it’s not all doom and gloom. Organizations can and should plan ahead so that they have both, strong data protection and detection capabilities as well as a robust plan for recovery in place as part of their cyber resiliency and risk management strategies.
Many of OECM’s IT-focused supplier partners offer products and services to assist OECM customers with cybersecurity planning and risk management, including support and resources that can help organizations better prepare to keep cyber threats at bay while protecting their people and businesses for the long term.
Check out these offerings available through the following agreements and supplier partners:
Cloud Technology and Related Professional Services
Awarded Supplier Partners:
| Carahsoft Technology Corp. | IBM Canada |
| Compugen Inc. | iVedha Inc. |
| Computacenter TeraMach Inc. |
Support & Resources Offered:
Access to public cloud Infrastructure-as-a-Service (IaaS)
- Provides the ability to provision processing, storage, networks, and other computing resources
- Managed network, storage, and server with the managed technology refresh cycle
- Virtual machines
- Secure, dual-factor method of remote access
- Appropriate patch management
Platform-as-a-Service (PaaS), which is a resource that provides the ability to deploy onto cloud infrastructure organization-created and will adhere to Customer’s security policies such as:
- NIST (National institute of Standards Technology) Cybersecurity Framework
- CIS (Center for Information Security) Controls v7
- ISO (International Standards Organization) 27001/27002 Cybersecurity Framework
- SOC (Systems and Organization Controls) 2/3 Auditing Framework
- CSA Star level 2 (with certification performed by a CSA- accredited certification body)
- COBIT (Control objective for information and related technology) Cybersecurity Framework
Electronic Device Disposal and Recycling Services
Awarded Supplier Partners:
| Compugen Finance Inc. | Greentec International Inc. |
| eCycle Solutions Inc. | Quantum Lifecycle Partners LP |
| ERS International |
Support & Resources Offered:
The agreement will help our customers conveniently and securely manage their electronic device waste through IT asset disposition, secured media destruction, and electronic waste recycling.
Awarded suppliers under the agreement offer pick up, disposal, and recycling services through secure transport, as well as media destruction services by mechanically destroying the data bearing devices securely using appropriate methods.
Electronic Document and Records Management Solutions
Awarded Supplier Partners:
| Coginov Inc. | Ricoh Canada Inc. |
| Konica Minolta Business Solutions (Canada) Ltd. | ThinkDox Inc. |
| Levio Conseils Inc. |
Support & Resources Offered:
Access to:
- Electronic Document and Records Management System
- Annual Maintenance and Licensing
- Digitization Services to convert physical records into digital-ready records
- Professional Services
- Consultation, implementation support and training to ensure solutions are accurately designed using best practices
Supplier will allow customer defined users the ability to control actions performed on records and by whom, including but not limited to:
- Manage Security groups based on user roles
- Identify the access and right of users within solution
- Apply security rules to the content based on user role or assigned classification
- Add extra level of security to document as required
- Control what actions can be performed on records
- Restriction on the ability to modify stored, declared records and their associated metadata
End-User Computing Devices and Services
Awarded Supplier Partners:
| CDW Canada |
| Compugen Inc. |
| Dell Technologies |
Support & Resources Offered:
Scope includes data protection and security where resources related to data backup, protection applications, security solutions, and security applications are provided.
IT Project-Based Professional Services
Awarded Supplier Partners:
| 01 Millennium Consulting Inc. | FlexITy Solutions Inc. | Levio Conseils Inc. |
| A.T. Consulting & Recruiting Inc. | Green PI Inc. | Procom Consultants Group Ltd. |
| Bell Canada | iVedha Inc. | Tech Mahindra Ltd. |
| Execute Strategy Inc. |
Support & Resources Offered:
Support for various IT Projects:
- Infrastructure Services
- Network Services
- System Integration
- Quality Assurance and Testing
- Additional IT Project-Based Related Professional Services (e.g., Audit and Compliance, Business Intelligence, Cloud Migration, Data Management, IT Disaster Recovery)
Access to cybersecurity-related professionals:
- Penetration Tester
- Security Analyst
- Security Architect
IT Technical Resource Augmentation Services
Awarded Supplier Partners:
| Calian Ltd. | Randstad Interim Inc. | Tundra Technical Solutions Inc. |
| David Aplin Group | S.i. Systems Partnership | Ward Technology Talent Inc. |
| PlanIT Search Inc. | Step by Step Professional Services Inc. |
Support & Resources Offered:
Supplier partners offering skilled resources to meet temporary IT needs:
- Over 20 roles, four different experience levels, and the flexibility to screen, test and replace candidates
- Access to professionals who can work on-site or from a remote location
- Dedicated account executive to provide day-to-day administrative support
Access to cybersecurity-related professionals:
- Vulnerability Assessment Specialist
- Security Analyst
- Security Architect
- Security Specialist
- Penetration Testing Specialist
Networking Products and Related Services
Awarded Supplier Partners:
| Access 2 Networks Inc. | Eclipse Technology Solutions Inc. | Long View Systems Corp. |
| Bell Canada | FlexITy Solutions Inc. | Netagen Communication Technologies Inc. |
| Calian Ltd. | Hypertec Systems Inc. | Northern Micro Inc. |
| CDW Canada | IBM Canada | OnX Enterprise Solutions Ltd. |
| Cloud Managed Networks | INSA Corp. | Secure Links |
| Compugen Inc. | Integra Data Systems Corp. | Secure Sense Solutions Inc. |
| Computacenter TeraMach Inc. | ISA Cybersecurity Inc. | Softchoice Canada Inc. |
| Dell Technologies | Lanworks Inc. |
Support & Resources Offered:
Access to the latest physical and virtual networking products, including license subscriptions.
Products available from 23 supplier partners, including:
- Access point products
- Routers
- Switches
- Security products
- Hybrid Networking Products (e.g., SDWAN)
- Wireless LAN Controller products
Access to OEM products compatible with different IT environments, designs and infrastructure, to meet current established open standards.
Related Services:
- Technical support services
- Block resource hours
- Onsite support services
- Preventive maintenance and proactive diagnostics
- Professional resources for network design and planning, installation and implementation and training
- Software updates and hardware replacement
Software License Products and Related Services
Awarded Supplier Partners:
| CDW Canada |
| Computacenter TeraMach Inc. |
| Softchoice Canada Inc. |
Support & Resources Offered:
Cybersecurity-related software available including, but not limited to:
- Cisco
- CrowdStrike
- Forcepoint
- Proofpoint
- Variphy
- Varonis
- Arctic Wolf
- FireEye
- RSA
- Palo Alto
Please contact OECM Customer Support or the supplier partner with specific software questions.
Vulnerability Assessment and Penetration Testing Services
Awarded Supplier Partners:
| 3Tenets Consulting Inc. | CDW Canada | iVedha Inc. |
| BDO Canada LLP | Computacenter TeraMach Inc. | |
| Bell Canada | IBM Canada |
Support & Resources Offered:
Vulnerability Assessment Services:
- Assess current network security measures to identify any vulnerability in the customer’s network
- Conduct external and/or internal vulnerability scans to identify security vulnerabilities in customer’s assets and resources
- Web application, website, wireless, and/or personal security awareness assessments and report security issues that post an imminent threat as they are being identified
- Vulnerability assessment report upon completion, the supplier will confirm detailed reporting requirements with the customer prior to commencement
Penetration Testing Resources
- Simulated cyberattack in an attempt to breach and exploit IT intentionally security
- Application penetration
- Network penetration
- Social engineering
- Web application
Optional Resources, including but not limited to:
- Cloud assessment and penetration testing
- Compromise assessment
- Device penetration testing
- Dynamic application security testing
- Security awareness training
- Threat risk assessment
Cybersecurity: What’s the Outlook?

Tight budgets and stretched resources – particularly in today’s ‘always on’ online world – can make it a challenge for organizations to keep up with new threats, as well as defence strategies, that seem to be emerging every day. However, it’s important to note that the threat isn’t going away. According to the World Economic Forum, in their Global Cybersecurity Outlook 2023, 86% of business leaders and 93% of cyber leaders believe that global geopolitical instability is likely to lead to a catastrophic cyber event in the next two years.
So, what should organizations focus on as they prepare?
As highlighted in the Government of Canada’s National Cyber Threat Assessment 2023-2024, “cyber threats can be mitigated through awareness and best practices in cybersecurity and business continuity.” Further, their assessors note that “cyber threats and influence operations continue to succeed today because they exploit deeply rooted human behaviours and social patterns, not merely technological vulnerabilities. Defending against cyber threats and related influence operations requires addressing both the technical and social elements of cyber threat activity.”
Working with a trusted third-party IT expert partner is vital to ensure that both types of vulnerabilities are detected and remediated before they are exploited by malicious threat actors. Using a holistic risk-based cyber approach can help organizations ensure they are supporting compliance and sound governance while cost-effectively addressing real-world risks and balancing those risks against other critical outputs, such as ensuring timely, effective, and efficient services.
OECM continues to work to facilitate opportunities for collaboration, transparency, and the timely exchange of information between suppliers and customers so that we can help you better identify and tackle supply chain and industry challenges and areas of impact.
If you have any questions about cybersecurity support and resources available through OECM agreements, please contact our Customer Support team at:
OECM Customer Support
1-844-OECM-900 (1-844-632-6900)
Check out OECM’s Industry Spotlight: Focus on Cloud Technology and Computing for more great supplier partner insights.
